A hacker allegedly behind a spate of Twitter account hacks on Wednesday gained access to a Twitter “admin” tool on the company’s network that allowed them to hijack high-profile Twitter accounts to spread a cryptocurrency scam, according to a person with direct knowledge of the incident.
The account hijacks hit some of the most prominent users on the social media platform, including leading cryptocurrency sites, but also ensnared several celebrity accounts, notably Bill Gates, Jeff Bezos, Elon Musk and Democratic presidential hopeful Joe Biden.
Vice earlier on Wednesday reported details of the Twitter admin tool.
A Twitter spokesperson, when reached, did not comment on the claims. Twitter later confirmed in a series of tweets that the attack was caused by “a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.”
A person involved in the underground hacking scene told TechCrunch that a hacker, who goes by the handle “Kirk” — likely not their real name — generated over $100,000 in the matter of hours by gaining access to an internal Twitter tool, which they used to take control of popular Twitter accounts. The hacker used the tool to reset the associated email addresses of affected accounts to make it more difficult for the owner to regain control. The hacker then pushed a cryptocurrency scam that claimed whatever funds a victim sent “will be sent back doubled.”
The person told TechCrunch that Kirk had started out by selling access to vanity Twitter accounts, such as usernames that are short, simple and recognizable. It’s big business, if not still illegal. A stolen username or social media handle can go for anywhere between a few hundred dollars or thousands.
Kirk is said to have contacted a “trusted” member on OGUsers, a forum popular with traders of hacked social media handles. Kirk needed the trusted member to help sell stolen vanity usernames.
In several screenshots of a Discord chat shared with TechCrunch, Kirk said: “Send me @’s and BTC,” referring to Twitter usernames and cryptocurrency. “And I’ll get ur shit done,” he said, referring to hijacking Twitter accounts.
But then later in the day, Kirk “started hacking everything,” the person told TechCrunch.
Kirk allegedly had access to an internal tool on Twitter’s network, which allowed them to effectively take control of a user’s account. A screenshot shared with TechCrunch shows the apparent admin tool. (Twitter is removing tweets and suspending users that share screenshots of the tool.)
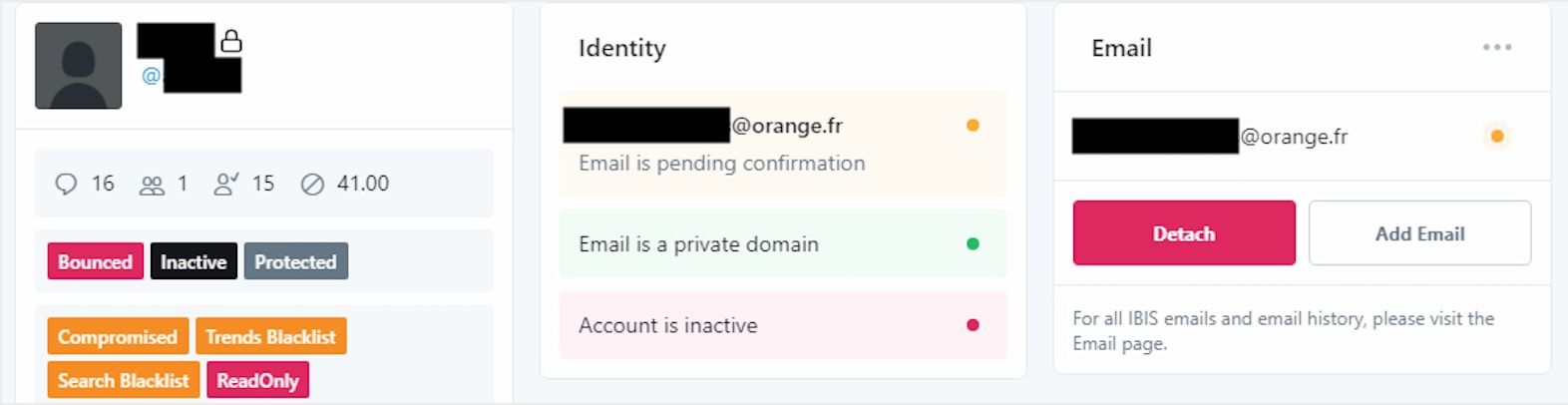
A screenshot of the alleged internal Twitter account tool. (Image supplied)
The tool appears to allow users — ostensibly Twitter employees — to control access to a user’s account, including changing the email associated with the account and even suspending the user altogether. (We’ve redacted details from the screenshot, as it appears to represent a real user.)
The person did not say exactly how Kirk got access to Twitter’s internal tools, but hypothesized that a Twitter employee’s corporate account was hijacked. With a hijacked employee account, Kirk could make their way into the company’s internal network. The person also said it was unlikely that a Twitter employee was involved with the account takeovers.
As part of their hacking campaign, Kirk targeted @binance first, the person said, then quickly moved to popular cryptocurrency accounts. The person said Kirk made more money in an hour than selling usernames.
To gain control of the platform, Twitter briefly suspended some account actions — as well as prevented verified users from tweeting — in an apparent effort to stem the account hijacks. Twitter later tweeted it “was working to get things back to normal as quickly as possible.”


No comments:
Post a Comment